Microsoft recently deprecated their PowerBI power packs for Microsoft Defender ATP, which were nice to have pre-built dashboards to use. Instead, they have provided guidance on how to pull date out of Defender ATP into PowerBI using custom queries, which can be found at this link.
When doing this though, I ran into an authentication issue that was blocking me from performing a query against Defender ATP. I am not going to rehash what Microsoft has already documented, so referencing the link above provides the details to how I get to the authentication issue below.
After creating the custom query, PowerBI Desktop prompts for credentials to authenticate to Defender ATP. Providing my credentials, and completing my MFA challenge, I appeared to be blocked by Conditional Access.

For more background, I am trying to access using my partner laptop, not a computer issued by my customer. We do have Conditional Access policies that require both an Intune Compliant device as well as a Hybrid Azure AD Joined device, both conditions my partner laptop do not meet. But, my user account is excluded from these policies.
Looking at the error message, this is clearly a Conditional Access message. So the first place I looked was the Azure AD sign-in logs. Looking here, it does indicate a Conditional Access failure, but the message was very generic. The sign-in code being 50131 with a generic message of Used in various conditional access errors. These provided no guidance.
Looking at the Conditional Access tab, all policies reported either Success or Not Applied, which made the error confusing. The message clearly indicates Conditional Access failing, but the policies in the sign-in log all showed they were not blocking me.

Using one of my customer's computers though, I had no problem running my PowerBI query. This told me that something was taking the device state into consideration, but as mentioned, my account was excluded from the only Conditional Access policy used to require trusted devices.
It was at this point I reached out to Microsoft, which put me in touch with an Azure AD product engineer. They were able to review the sign-in logs on the backend systems based on the Request ID and identified it was Conditional Access blocking access. But, it was not any policy I created, but an old remnant from the past...
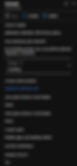
Before the new Azure model using the Azure Resource Manager (ARM) model, there was a Classic Azure portal. At that time, default Conditional Access policies were created automatically for a tenant. Strangely enough, there was one created that applied to Windows Defender ATP.
We are unable to view the old Classic Azure portal, but these Classic policies are visible in the new Azure portal. Sure enough, there was one named [Windows Defender ATP] Device Policy, which requires a "known" device. This was not clear whether it was a trusted (Intune Compliant or Hybrid AAD Join) or simply an AAD registered device. We cannot actually configure or even see the settings of this policy. The only options we have are to disable it or modify the group scoping.
The Classic policy can only be scoped using groups, not users directly. Therefore, I created a quick group, added my account, and added that group as an Exclusion. Sure enough, everything worked.
The only word of caution is that you do have the option to Disable the policy all together. If you disable a Classic policy, it is disabled permanently. Once disabled, you can not reenable it. Not that the policy may really be necessary anymore as standard Conditional Access policies will be able to address any security needs, but you may want to test before simply disabling.
